Step 2. The first screen of the Format Windows Vista sequence will show up. At this point you need to select your Language and Time and currency format (click the image to enlarge). Press Next.
Step 3. Press Install Now
Step 4. After a min you will be asked for your Product Key.
Scenario 1: If you don’t have your product key, you can skip this step and at the next step you will be asked to pick Vista Package that you want to install : Vista Home Basic, Home Premium, Business, Ultimate. If you install windows vista without providing product key, after 14 days you will have to enter a valid product key, or if you don’t, you’ll be forced to format windows vista again. This is good if you want to test which windows vista version is best for you, before your purchase.
Scenario 2: You enter your product key (keep it handy!), and at the next screen your purchased version will be auto-recognized.
Step 5. Accept the Microsoft Windows User License Terms and press Next
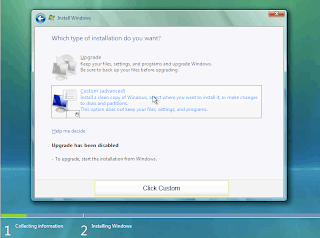
Step 6. Dialog – “Which type of installation do you want ?”
Scenario 1: If you already have another operating system installed (ex. Windows XP) you will have the Upgrade option enabled. It’s up to you to decide if you prefer “clean” install or upgrading from previous Windows Installation. Clean install is recommended for improving system performance, and Upgrade Setup is recommended if you have some files in your C: , My Documents, or Desktop folders that you don’t want deleted.
Scenario 2: You already have operating system installed but you want to format your drive, deleting the old system and installing fresh Windows Vista copy. In that case select the C: drive and press Format ( don’t format all drives! only the primary where we are installing Windows Vista – ” C: “. The setup will do the rest.
Step 7. Select Disk 0 and click Next
Step 8. The copy process will begin. This process can take some time, so relax a bit, make a coffee or something :D . Your input won’t be required here for some time.
Step 9. After Windows Vista Setup finishes, the computer will reboot.
Step 10. Windows Vista files are copied , and now setup will configure Windows Vista for your PC. This step will take some really good time.
Step 11. Installing Windows Vista finishes, insert your User Name and Password here.
Step 12. Give your PC a name! and select one of the colorful backgrounds
Step 13. Select your preferred security settings. If this computer is not behind a firewall, the best option is the ” Use Recommended settings”. If you are using firewall then you can select “Install important updates only” (Windows Update). If you want to be protected and your Windows Vista to have the latest updates from Microsoft , select the first option.
Step 14. Select your time zone and location.
Step 15. Network Configuration – Select your computer location. This settings sets your network permissions.
Step 16. This is self explanatory :) Welcome to your new Windows Vista Operating System
Step 17. After you press Start, some Windows Vista settings will be upgraded automatically.
Step 18. You now need to install some drivers that the system will not install automatically.
Finished.